Justaddwater.dk hacked
The non-technical version:
Last Thursday we unfortunately had an intruder on Justaddwater.dk. The cracker used a flaw in our blogging software to gain administrative access to it. With this access the cracker placed a secret backdoor on the server.
It seems that the intention of the cracker where to use our server to host illegal copies of movies as part of a larger pirate network. To our luck the technical skills of the cracker where very bad (read: script kiddie) and the attempt to upload files to our server was not successful. The cracker therefore quickly gave up and did not try to access to backdoor afterwards.
We have now upgraded our blogging software to the newest version effectively closing the security hole and have reverted his (or hers?) changes and damage to the system.
We have tried to track his every move in our system, but cannot guarantee that he at some point didn’t get a copy of all our commenter’s e-mail addresses. We are pretty sure he was not after this information, and it does seem like he did not retrieve them, but we are not a 100% sure.
I know some of you use unique e-mail addresses when writing comments on our blog. If you are such a person and ever get any spam on this unique e-mail address, we would very much like to hear from you.
To those of you who subscribe to our newsletter, you can rest assure that your e-mail addresses where never in any danger. They are safely kept at our service-providers and the intruder have not had access to them.
For more information on how we store user information see our Privacy Policy.
Info to fellow WordPress users
The versions of WordPress affected by this security issue are:
- The entire version 2.1.x branch
- In the 2.0.x branch, every version below 2.0.11 is affected
If you are still running WordPress version 2.1.x we urge you to quickly upgrade to a newer version (2.2 or above). If you are running the older 2.0.x branch you can upgrade to version 2.0.11.
All the technical goodies
The bug in question is a serious SQL injection bug affecting /wp-admin/admin-ajax.php where the attacker can perform any SQL command on your WordPress database (including wiping it out completely!).
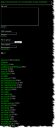
In our case the cracker “only” used it to gain administrative WordPress access and updated the WordPress “upload_path” to point to the servers /tmp directory. He then uploaded a PHP script to this folder and added it as a WordPress plugin by manipulating the “active_plugins” option in WordPress. The purpose of this plugin was to lay dormant until a call to a specific URL was detected. This secret URL would then render a backdoor interface instead of the regular justaddwater.dk. You can see the backdoor interface by clicking the thumbnail below:
After looking at the Apache log files we can see what the cracker actually did to gain access and what he used that access to do.
First he made a very strange call:
[code]”GET /wp-includes/js/tinymce/wp-mce-help.php HTTP/1.0″ 200 7411 “-” “-“[/code]
I have no idea why he called this URL first. My guess first was that this was a way of detecting which version of WordPress we where running, but after investigating I can see that this file exists also in versions not affected by the bug.
Secondly he called the URL affected by the SQL injection bug several times (actually 159!):
[code]”POST /wp-admin/admin-ajax.php HTTP/1.1” 200 2 “-” “Mozilla/4.0 (compatible; windows 5.1)”[/code]
Every call looks the same except for the size of the response in bytes following the 200 response code (in the above log entry it’s 2, but sometimes it would be 298 or 299). It would have been during these calls that the cracker gained administrative access to WordPress. The cracker also created a new post that he would later use as a placeholder for the PHP script he where to upload.
Now followed 8 calls to options.php:
[code]”POST /wp-admin/options.php HTTP/1.0” 200 1248 “http://justaddwater.dk/wp-admin/options.php” “Opera”[/code]
Notice how the user-agent changes all the time. This could be different scripts running, set to identify them selfs differently. My guess is that he used these calls to change the “upload_path” option and the “active_plugins” option. He could have done this via SQL injection though.
Then came 10 calls to upload.php, the script used to upload pictures etc. to posts:
[code]”POST /wp-admin/upload.php?style=inline&tab=upload&post_id=-1 HTTP/1.0″ 200 1150 “http://justaddwater.dk/upload.php?style=inline&tab=upload&post_id=-1” “Opera”[/code]
My guess is that he used these calls to upload the backdoor script to /tmp. Why he needed 10 I don’t know.
Then came another 15 calls to options.php:
[code]”POST /wp-admin/options.php HTTP/1.0” 200 1230 “http://justaddwater.dk/wp-admin/options.php” “Opera”[/code]
It’s not quite obvious why he made these last calls, except to maybe clean up something he made earlier.
Now came a very strange call to upgrade.php that I can’t figure out why he made:
[code]”GET /wp-admin/upgrade.php?step=1 HTTP/1.0” 200 1172 “-” “-“[/code]
This script is used to upgrade the WordPress database after installing a new version of WordPress. He might have used some of the previous requests to prepare an “upgrade” script that he could then run this way, but why didn’t he just use the SQL injection technique from before?
Finally he accessed his newly created backdoor, looked inside our /wp-content folder, did 3 POSTS (that I suspect where file-upload attempts) and then left never to be seen again.
Technorati Tags: script kiddie, hacking, hacker, cracker, WordPress, security, justaddwater.dk, bug, blogging software, hacked, vulnerability, apache, log files

November 15th, 2007 at 02:07 (GMT-1)
Im thinking that my GermWorks website has also been hacked as I now get an error message saying that the database is not connected :(
November 27th, 2007 at 10:53 (GMT-1)
Really good and really interesting post. I expect (and other readers maybe :)) new useful posts from you!
Good luck and successes in blogging!
November 28th, 2007 at 21:11 (GMT-1)
The same thing happened to Al Gore recently. See The Register:
http://www.theregister.co.uk/2007/11/27/climate_change_hack/
(via http://photomatt.net/2007/11/27/al-gore-hacked/ )
November 29th, 2007 at 10:34 (GMT-1)
[…] a big challenge. But we actually tried that recently when Justaddwater.dk got hacked. The hacker used a security hole in an old version of WordPress and to upload his malicious code, […]
March 1st, 2008 at 09:19 (GMT-1)
Really very informative post, I am using older version of wordpress for my 3 blogs (linux,php and seo). I also need to upgrade my wordpress version to ensure the security of my blogs.
Thanks much for the great info…
March 23rd, 2008 at 22:11 (GMT-1)
Wow. I didn’t even know flaws like this were possible in WorldPress.
I’m not technical…what kind of background would someone need to detect this kind of intrusion? I’d like to have my site checked, but don’t know where to look.
March 30th, 2008 at 22:08 (GMT-1)
[…] Justaddwater.dk hacked […]
May 16th, 2008 at 06:36 (GMT-1)
[…] Justaddwater.dk hacked […]
May 21st, 2008 at 11:14 (GMT-1)
Sorry about the intrusion, Thomas, and better luck with the site in the future. What I can add is to make a copy of the db as often as possible.. sites will always be cracked, so it is important to be able to restore. There is a plugin to send a backup of the db via email and worth looking into.
Other than that, the debugging /hack tracing skills of yours are impressive. Thanks for the detailed explanation.
steve
May 26th, 2008 at 00:43 (GMT-1)
This is quite informative. I’m sorry about the hacking incident, I’ve personally gotten hacked by random people across the net multiple times in my forum . I used Vbulletin–I realize that I had to update almost immediately when Vbulletin came out.
But it’s great that you can actually diagnose your hacked hole!
June 10th, 2008 at 10:44 (GMT-1)
This shows the importance of regularly checking your logs for signs of suspicious activity against a baseline. I wish someone would release a simple hosted service (like statcounter) that would identify anomalies like this in realtime.
-Kris
July 25th, 2008 at 02:59 (GMT-1)
I use WP version 2.5 for my blog. Has anybody ever heard of this happening in this version? I see they just came out with a 2.6. I will upgrade immediately just in case. Thans for the info!
August 4th, 2008 at 14:45 (GMT-1)
I use wp versiyon 2.6.It seems very safe ;)
August 8th, 2008 at 18:06 (GMT-1)
nice article, gonna try it ;)
January 10th, 2009 at 04:56 (GMT-1)
google and wordpress are getting better at stopping these crackers. the worst ones are where everyhting seems normal to you, but to google, there are 100 links to spam sites. wordpress are making it easier to upgrade, and google will attempt to notify you if they detect any malicious ocde.
January 16th, 2009 at 00:37 (GMT-1)
Wow that sucks. Glad to know you were able to close the security hole though.
February 10th, 2009 at 02:49 (GMT-1)
It is normal to find such this attacker. i think you must give care for the www apache server and also about the injections technice
October 21st, 2009 at 13:17 (GMT-1)
WordPress is new update available, in version 2.8.5 more security issue fixed…